Hacking and Security
-
Khabar Foori (Breaking News) Channel and malware distribution
⭕️ This is Dr. Mostafa Entezari, the manager of Breaking News (Khabar Foori) media (Telegram channel and news website and…
Read More »
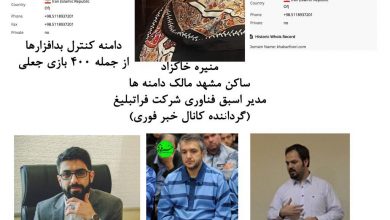
⭕️ This is Dr. Mostafa Entezari, the manager of Breaking News (Khabar Foori) media (Telegram channel and news website and…
Read More »